11 | Add to Reading ListSource URL: jon.oberheide.orgLanguage: English - Date: 2015-10-18 22:20:40
|
|---|
12 | Add to Reading ListSource URL: www.digitalcatapultcentre.org.ukLanguage: English - Date: 2016-03-09 06:12:58
|
|---|
13 | Add to Reading ListSource URL: www.parentpaperwork.comLanguage: English - Date: 2015-08-12 01:38:59
|
|---|
14 | Add to Reading ListSource URL: casc.orgLanguage: English - Date: 2014-09-20 14:38:00
|
|---|
15 | Add to Reading ListSource URL: www.onlinesbiglobal.comLanguage: English - Date: 2012-03-24 07:21:16
|
|---|
16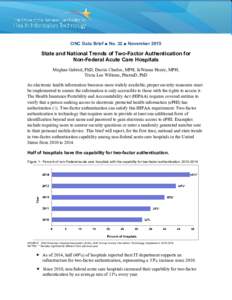 | Add to Reading ListSource URL: www.healthit.govLanguage: English - Date: 2015-11-18 11:27:14
|
|---|
17 | Add to Reading ListSource URL: discovery.ucl.ac.ukLanguage: English - Date: 2015-07-21 04:21:47
|
|---|
18 | Add to Reading ListSource URL: www.ciosummits.comLanguage: English - Date: 2016-01-25 16:20:59
|
|---|
19 | Add to Reading ListSource URL: www.cryptsoft.comLanguage: English - Date: 2016-02-25 10:46:48
|
|---|
20 | Add to Reading ListSource URL: fc13.ifca.aiLanguage: English - Date: 2013-03-27 20:42:00
|
|---|